Manage signing certificates
You can manage signing certificates using the 10Duke Scale UI console.
Signing certificates enable you, the vendor, to request X.509 certificates for license token signing keys. Using certificates improves security by enabling key integrity verification. The full certificate chain for a license token signing key is responded in the JSON Web Keys API endpoint (see RFC 7517). By embedding the trusted signing certificates in your licensed client application(s), the applications are able to check that the license token signing key certificate chain has such a trusted certificate at the root of the chain. Doing this before accepting signature check results of license tokens increases the security of your applications.
10Duke Scale signing certificates are valid for five years at a time. You can generate a new certificate for example every two or three years apart and switch to using the new certificate for signing license token signing certificates. This rotation should be coupled with symmetrically renewing the trusted certificates you embed into your application(s).
Limitations
The 10Duke Scale functionality related to signing certificates is based on RFC 2580. It is important to check the information in RFC 2580 on the limitations such as the upper bounds. The validation of field values in 10Duke Scale UI console checks the field value lengths as well as applies limitations to the use of characters. If you enter invalid values, the UI console shows validation errors.
View signing certificates in the UI console
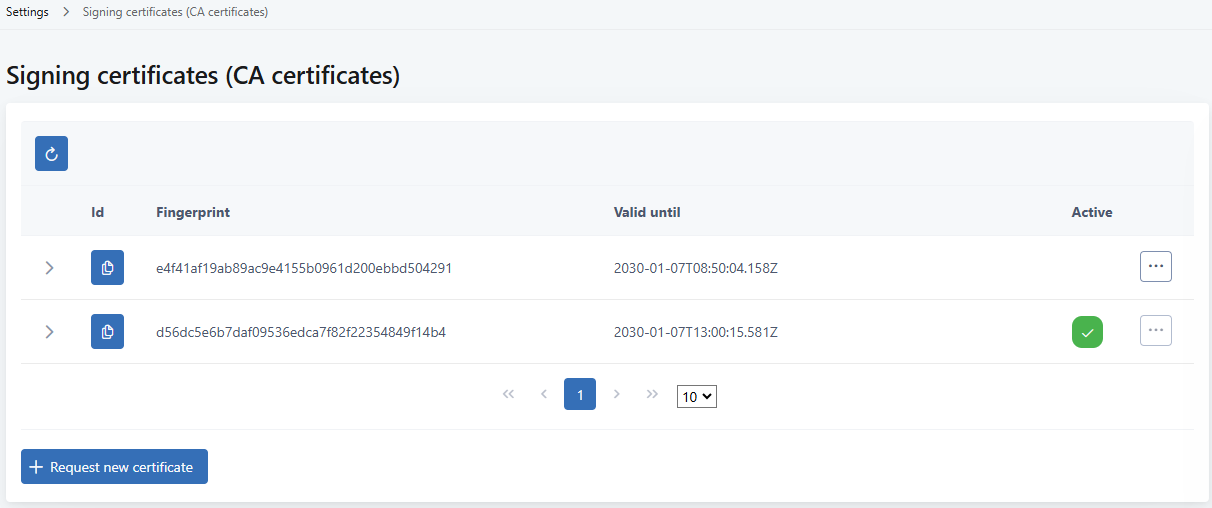
To view the signing certificates:
-
In the left siderbar, go to SETTINGS > Signing certificates.
A list of your certificates opens. The list shows which of the signing certificates is currently active.
-
To view the signing certificate, click the arrow icon to expand the row.
The three-dot menu on the list provides options for setting an inactive signing certificate as active, and deleting an inactive certificate.